 Unit 2 - Activity 1 Introduction to Computing virtual identities
Unit 2 - Activity 1 Introduction to Computing virtual identities
Activity Overview
This discussion allows students to learn about the constraints and affordances of virtual identity systems through the perspective of computer science terminology and discuss ethical issues around corporate data collection practices.
Key Terms and Concepts
Key Takeaways:
Driving Questions:
Materials and Preparation:
MATERIALS
- Computer
- Projector
- Alternatively: Print handouts of Facebook advertising preferences page
Activity Instructions
- Review discussion on various types of virtual identities (15 minutes)
- What are the differences in structure and content between virtual identity as avatar, social media profile, and data profile? Who creates each of them?
- What do you focus on in each of these virtual identies? What are the constraints and limitations of these systems? What aspects of your identity are you not able to represent?
- Facebook Virtual Identity Discussion (35 minutes)
- Navigate to: https://www.facebook.com/ads/preferences/?entry_product=ad_settings_screen
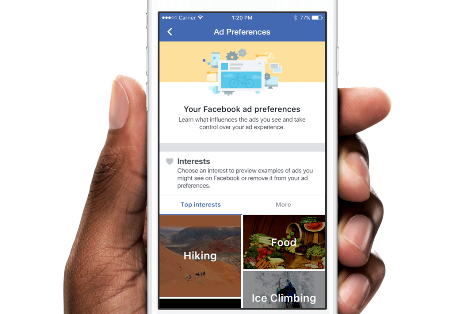
- Discuss as a group: What is contained in our Facebook ad profiles? Why do these profiles exist, and how do websites like Facebook make money? How is this information is collected? Is this our real self? Do you want it to be accurate or not?
- When we talk about data on people, this is not typically seen by anyone.
- Only recently are facebook and google showing their advertising categories, but this is not the complete profile that is stored on you. Anytime you visit a page with a facebook share button, it tells Facebook. Some companies also use “pixels”. Incognito browser mode keeps it out of your history but you’re still trackable by these websites.
- ASK: What is the purpose of companies collecting and maintaining data profiles on people?
- ASK: Should people always have access to this type of information on themselves? Should people have to consent to have this data sold? Is it important for it to be accurate? Why?