 Unit 2 - Activity 2 Developing Front & Back End Virtual Identities
Unit 2 - Activity 2 Developing Front & Back End Virtual Identities
Activity Overview
This activity provides a creative, interactive exercise following students’ identification of 3 fictional characters which represent them in which the class collectively creates a game avatar, social media profile, and corporate data profile for the fictional characters identified by the students. The discussion throughout this activity allows students to critically reflect upon the constraints and affordances of virtual identity systems and gain a new awareness of corporate data collection practices.
Key Terms and Concepts
Key Takeaways:
Driving Questions:
Materials and Preparation:
MATERIALS
- Computer
- (Optional) Projector
PREPARATION
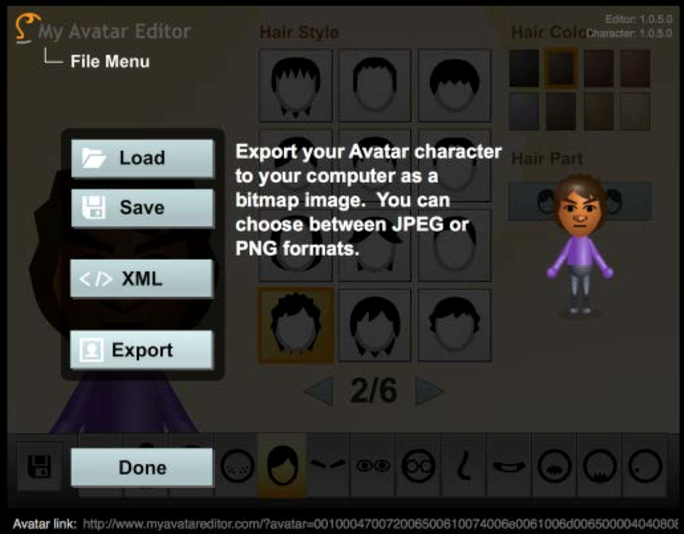
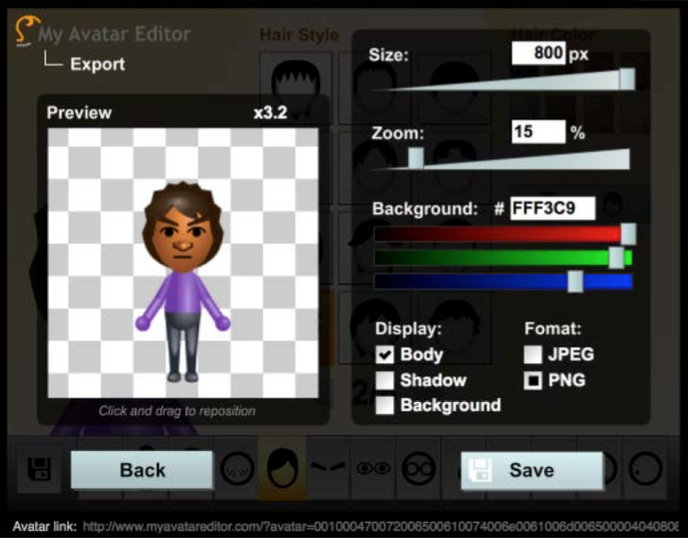
Instructors should identify an avatar design system for students to use as well as to analyze (in terms of the affordances, features, and constraints of the system). Instructors may want to provide instructions in the form of slides or a handout on how to customize and export the avatar as an image file.
Example Avatar Customization & Export Screenshots: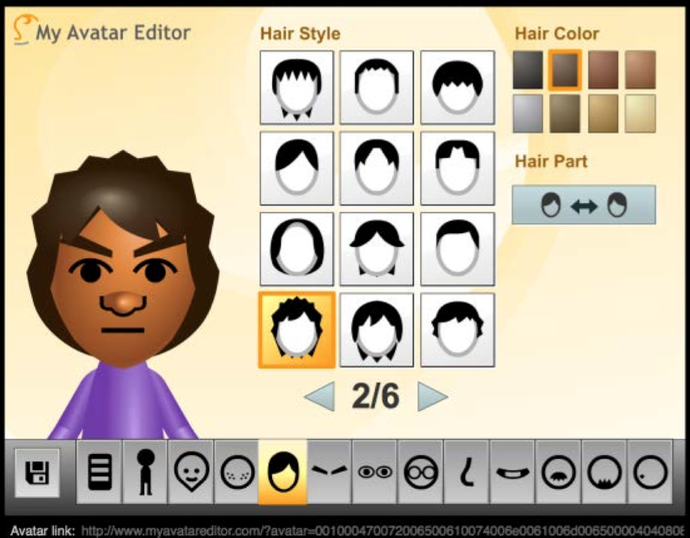
Activity Instructions
- Data Structures & Modularity (20 minutes)
- Our corporate profiles all have “back end” data: the image and the code/data structures that implement the “front end” data: the information that we see as users.
- Introduce students to the concept of modularity, both within the data structure and in the image: all the components are interchangeable. We could replace all the assets and the system would still function the same. You can also swap out functions.
- For example: Show what the Mii data structure looks like. Reflect on various parameters of the system (e.g.: “isGirl” is a Boolean which adds or removes a skirt from the avatar). How is this a good model and how is this a limited model? What are other ways of these avatar attributes being surfaced in the user interface (e.g.: a slider)?
- Show Facebook Interactive graph API interface for data profiles and discuss how the API describes the first four identity fields.
- Group Avatar and Profile Creation (40 minutes)
- Have a student volunteer to come up to the front of the room and as a group, create a game avatar, a social media profile, and a corporate data profile for one of the fictional characters that the student chose (if multiple students want to share or a student wants to blend three fictional characters together, that’s fine).
- Game Avatar (10 min)
- Create a mock game avatar image of the fictional character.

- For example, you can use the Nintendo Mii creator online to create an avatar of the character that might be used in a game.
- ASK: What kinds of games do you see avatars and virtual identities being very important to? Why?
- ASK: What aren’t we able to do or express about your character in particular avatar creation systems?
- Social media profile (15 min)
- Create a mock social media profile page for the fictional character.
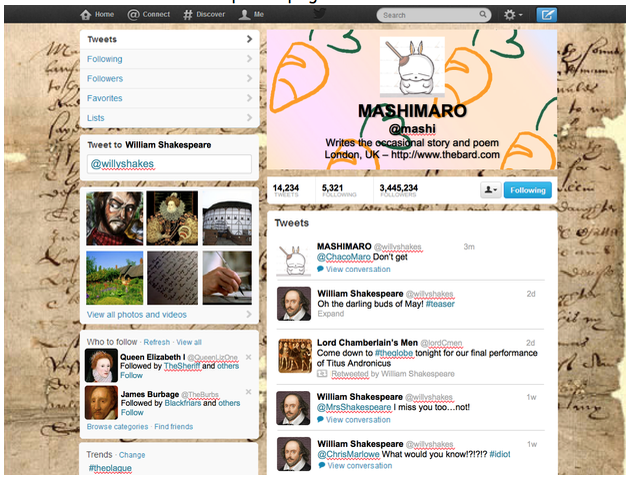
- For example, you can make a fake Twitter account page in Powerpoint or Google Slides and give one of the characters a location, a follower count, their profile picture, often a picture of them, their cover photo, often an abstract image that represents something about them, pinned tweet, other tweets, bio, location, links to other accounts in the bio. Discuss how the profile would differ if you were making it for Snapchat? For Instagram? For Linkedin? For YouTube? For Etsy?
- ASK: What are the most important parts of people’s social media profile pages? For example, when you look at someone’s Twitter profile, where do you look first?
- ASK: Do you find yourself thinking of your social media profiles as your self? What about for other people?
- Corporate Data Profile (25 min)
- Create a mock corporate data profile (e.g.: to track advertising preferences) of the fictional character.

- For example, attempt to characterize the character’s Facebook ad preferences: https://www.facebook.com/ads/preferences/?entry_product=ad_settings_screen
- When we talk about data on people, this is not typically seen by anyone.
- ASK: What kind of information might be useful for an advertiser, or an intelligence agency, for that matter, to know? Would you consider this a virtual identity?
- Create a mock game avatar image of the fictional character.